As we all are already aware, the Russian invasion of Ukraine started (officially) on February 24th, 2022, and it came along the so-called, classic war, with many other new, developed, and extensive types of warfare: cyber, radio, psychological, financial, etc.
This time, I will show you a quick and very simple OSINT demo, of the AIS spoofing and GPS jamming in West side of the Black Sea region.
AIS stands for Automatic Identification System and is digitally broadcasted information data, over VHF, consisting of ship name, course and speed, classification, call sign, registration number, MMSI, and other information. The Bridge Officers onboard the vessels are then using such information, as an additional tool, for enhancing the ship’s safety navigation and operations.
Since navigation (maritime, aero, auto, etc) is mainly based on the GPS constellation, the obvious target and scope was to interfere with its functionality in certain areas of interest. GPSJam is a live source of such activities.
Other alternative navigation satellite constellations: Galileo (owned by the European Space Agency), BeiDou (owned by the Chinese state), etc.

Now, returning to our AIS topic, today, 10.07.2024, at 03:20 UTC, I did a quick research on some publicly available sources, and here is what I’ve got:
On Marinetraffic, on an overall view over the western side of the Black Sea, you may notice some unusual reported positions inside of the Crimea Peninsula, just NE of Sevastopol.

Zooming in a bit, you’ll observe that there is no “water” in the area, sea, lake or river).

Going to Google Maps, and finding the same location, you might wonder (or not), what few ships will do in the area of an airport… Simferopol Airport (between Rodykove and Ukromnoye area).
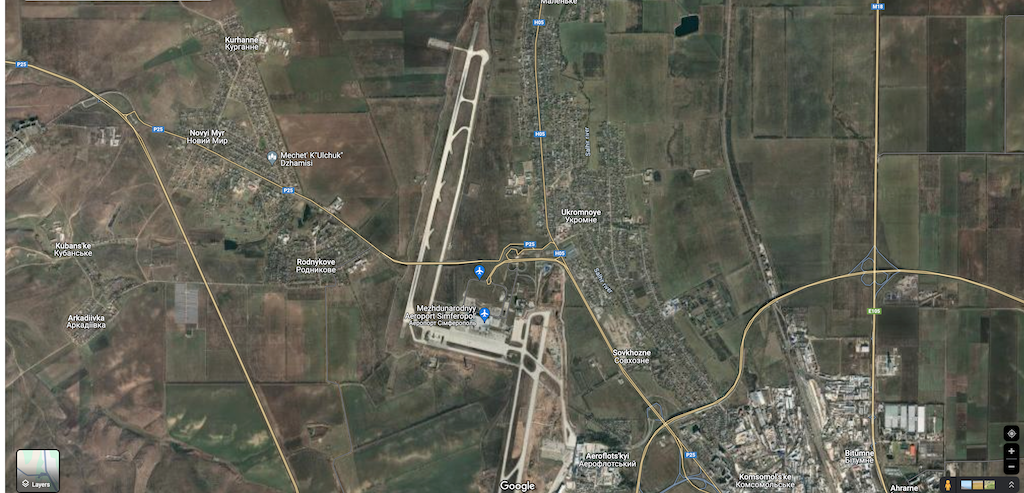
Then, I picked up randomly, an AIS of the bulk carrier, named “Magic L”.

To verify the data is accurate, I cheked the same AIS on Vesselfinder, and surprise, here the position on the map was correct.

As the minimum rule of 3rd, I check on another AIS marine traffic source, Shiplocation, and the confusion increased as pinpointing the ship’s name and AIS is resulted in double locations…

The air traffic is affected too due to the shorter response time needed for taking the proper actions, the maritime AIS traffic spoofing is meant to create confusion, traffic jams, chaos or even accidents.
An extensive OSINT & Radio survey will follow, so stay tuned and safe!
Later update: on October 24th, the national TV post, ProTV, confirmed my above statements: Sistemele de navigație GPS după care se ghidează avioanele în zbor au fost lovite intens de bruiaj. De unde vin interferențe.
InfoSec & ICT Maritime & SMB/SOHO:
















